Guardare Enters UKI Market Through Strategic Partnership
Read More →
Guardare integrates with your existing tools to create a complete view of your environment.
AI-driven analysis and human validation work together to surface hidden risks and prioritize what matters most.


Guardare plugs into the tools you already trust, like endpoint detection, firewalls, identity, cloud infrastructure, and more. In just a few minutes, you’ll have a unified view of your entire security environment without affecting any tools or systems already put in place.
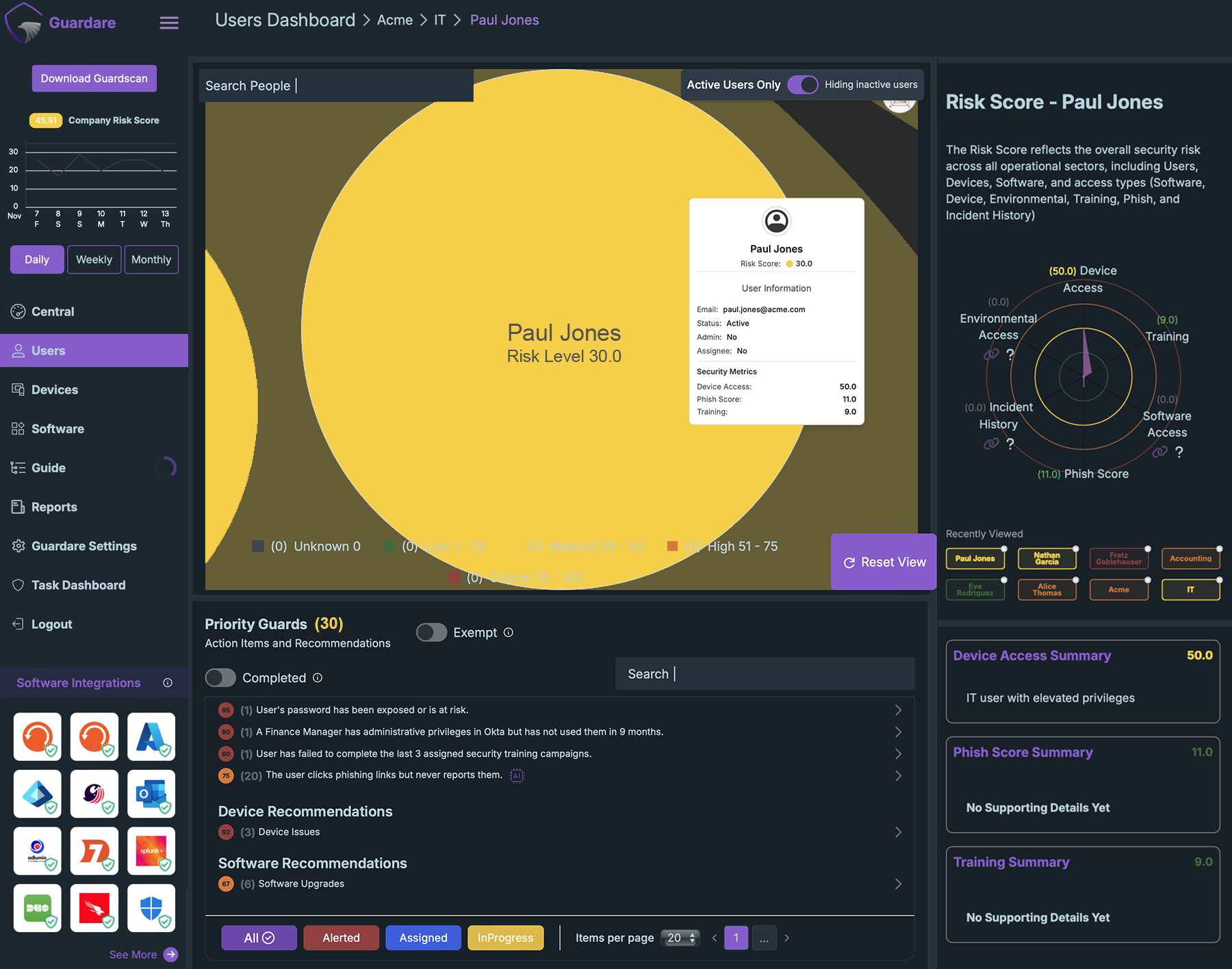
Our proprietary AI builds a unified risk graph of every user, device, and application. Guardare flags critical exposures and ranks them by business impact.
Natural language instructions tell you exactly what to do, in order of importance, to help lower risk. Whether it’s patching a device, tightening identity controls, or reconfiguring a firewall, Guardare helps teams act with confidence and reduce security risks faster.
Every action helps Guardare learn from global data and your environment to anticipate threats and improve your security posture.








We have spoken to thousands of organizations over the last 10 years regarding cybersecurity and reducing the risk of a successful attack.
Discover how our unified platform brings together your tools in your environment, helping you find hidden risks, reduce manual work, and strengthen security protection.
Schedule a custom demo to see how Guardare makes things easier for your business.
